We are a leading managed IT security services provider serving Toronto and the surrounding area.
Mitigate risk by letting HEM Solutions secure your infrastructure and monitor your network with our managed security services.
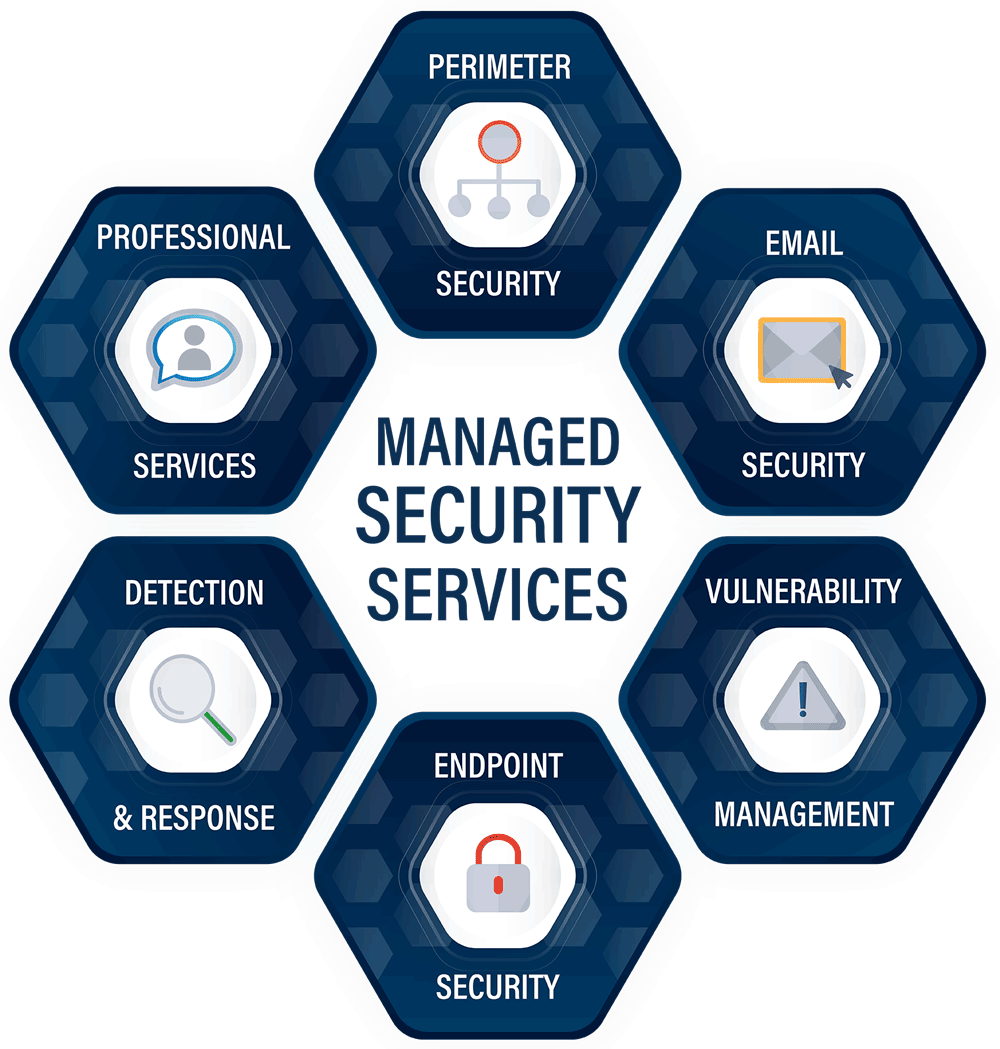
Premier Managed IT Security Services In Toronto
Our cutting-edge Managed Security & Monitoring services include: Risk and policy assessments to keep you informed of threats, while comprehensive penetration testing, firewall protection, and endpoint threat protection lock down your information.
Other Managed Security Protection services:
- Web Security Protection
- Intrusion Detection
- Log Mgmt
- Disaster Recovery
- Mobile Security
- Virtual Chief Security Officer
- Malware Remediation
- Patch Management
- Security Audit Control
- Breach Assessment
Malware is more dangerous than ever, and cyberattacks are becoming more frequent.
As technology evolves, hackers have more tools available to them. With advanced malware and limitless resources, hackers are making millions hacking and attacking small and large businesses, stealing their data, and taking their networks hostage. HEM’s Cybersecurity solutions protect your business with a combination of WAF firewalls, threat prevention tools, antivirus software, and more, for an affordable monthly fee.
Our cyber security solutions secure every aspect of your business, including your servers, workstations, apps, data, and employees. We are constantly monitoring the health of your networks and making sure you’re compliant with industry regulations like PHIPA Personal Health Information Protection Act and SOC.
HEM’s Cybersecurity solutions provides:
- WAF firewalls and intrusion prevention systems that can detect unusual network behaviour
- Antivirus software for detecting malware on desktops and mobile devices
- Email security software that keeps your inbox free of phishing scams
- Access restrictions for employees, departments, devices etc.
- Advanced encryption protocols for data
- Vulnerability assessments, and compliance management
- Ongoing network monitoring and maintenance









